A Systematic Approach to the Legal Evaluation of Security Measures in Public Transportation
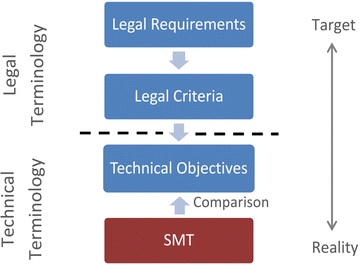
Fig. 3.1
Normative decision making
3.4 The Legal Evaluation of Security Measures
The guidelines presented in this chapter will enable a decision maker to perform a fundamental legal evaluation of existing and future security measures based on the schema distilled in the previous chapter.
Starting point of the evaluation method are the most permanent legal norms, which – through their fundamental and technology neutral nature – provide a framework for future societal developments. Such norms can be found in fundamental rights catalogues. Law below the constitutional level is not suitable as a basis for the method, as it can only be technology neutral to a certain degree.38 This means that due to the rapid progress of technology it antiquates quickly and thus cannot be used for the compilation of long-lasting guidelines. In addition to this, it is only concerned with a small part of the effects of technology usage.39 The life expectancy of such subconstitutional laws, especially those concerned with the use of technology, is therefore limited. Fundamental rights and principles however are long-lasting and offer a much more future-proof solution.40 In addition to this, they serve as guidelines for the interpretation of subconstitutional law.41 This is true in any legal system based on a hierarchy of norms (‘constitutional’ statutes versus ‘ordinary’ statues),42 as the fundamental rights and principles can be regarded as being the consented objectives of a society.
It is easy to agree that a technology should be socially acceptable. The quarrel begins where it has to be decided what it means exactly to be socially acceptable. But if the definition is based on fundamental rights and principles, which society has already agreed upon as its objectives, consented objectives for a technology design that minimises social conflicts are already predetermined.43 This underlines the logic behind using fundamental rights and principles as a basis.
However, these fundamental rights and principles do not contain statements that are directly applicable to technical systems.44 This means that the fundamental rights cannot be the immediate basis for the evaluation and the design of technology; they have to be concretised.45 This is where the established rules of legal interpretation come into play.46 As indicated above, the aim is not to ascertain the legality of a technology, but its legal compatibility. Ascertaining the legality of a technology means nothing more than saying that the use of a technology would be legal or illegal within a certain legal framework. In that case, there would be only black and white, which means that this approach is too narrow to provide assistance for a selection process. In contrast, legal compatibility is a broad approach which allows a grading: a technology can be more legally compatible or less legally compatible.47 It is thus a qualitative approach that allows for a differentiation within the concept of legality. This means that it is not identical with legality and not the opposite of illegality (Fig. 3.2).48


Fig. 3.2
The qualitative approach of the method
When talking about fundamental rights and principles, legal compatibility means compatibility of the underlying social conditions or requirements and of the impact of technological changes with the objectives of the fundamental rights and principles.49 The term is thus mostly synonymous with social compatibility, as social compatibility is defined as the compatibility with the objectives and standards of a society,50 whereas the law – and particularly the fundamental rights and principles – is the embodiment and formalisation of these objectives.51
By using the means of concretisation of fundamental rights and principles, the method faces the challenge of closing the description gap between broad and unspecific legal requirements – as found for instance in general clauses – and concrete design proposals,52 because such proposals cannot be found in abstract general clauses.53 To this end, the general clause, or in this case a fundamental right or principle, is concretised over several steps. Thereby only the legally relevant part of the technology or measure is covered, not the entire functionality.
The outcome of the use of the method can depend on the attitude of its user. This is due to the fact that different interpretations of legal norms exist.54 This effect can be minimised where the user follows the majority position when faced with a controversial question, especially the rulings of higher courts like the Court of Justice of the European Union. This approach is further advocated by the fact that it strengthens the result of the examination. Still, the use of the method will yield different but congeneric results, varying from user to user. This is a desired effect, because the method does not strive to be an automatism, but a guideline that allows for different emphases. The structured composition of the method guarantees traceability. Thus, the results of its use are derived in a clear way and can become a subject for discussion.
The use of the method is composed of four steps. Starting point of its use are the relevant fundamental rights and principles, which have to be identified and selected in a preliminary stage. What follows is a step by step concretisation of the fundamental legal provisions identified in the preliminary stage, at first into legal requirements, then in a second step into legal criteria and in the third step into technical objectives. The abstract legal requirements become more concrete with each step. Between the legal criteria and the technical objectives, a shift occurs from the terminology of the law to the terminology of technology.
As an exception, legal acts below the level of fundamental rights and principles may under certain circumstances also be used as a basis for the method, where they contain direct concretisations of fundamental rights and principles in the form of abstract general clauses.55 An example of this are the data protection principles found in the European Data Protection Directive.56 These are concretisations of Article 8 of the Charter of Fundamental Rights of the European Union.
3.4.1 Pre-stage – Identifying Fundamental Legal Provisions
First, in a pre-stage, the relevant fundamental legal provisions as the basis for the evaluation have to be identified. Within the European Union, the catalogues of fundamental rights found in the Charter of Fundamental Rights and in the European Convention on Human Rights can form that basis. Using the Charter as a basis is preferred to using the Convention, since the rights of the Convention are already included in the Charter which itself is based on the Convention. The Charter is more extensive and more up-to-date compared to the 50 year old Convention. It thus makes sense to base an evaluation on the Charter. However, the limits to the legal effect of the Charter have to be kept in mind.
Since the aim of the proposed method is a qualitative evaluation beyond minimum legal requirements, the Charter can serve as a guideline and basis for evaluation even where it is not directly applicable. The use of security measures in the context of aviation security is already subject to the provisions of the Charter.
Another possibility is to use national constitutions as a basis. This is possible wherever a constitution contains a catalogue of fundamental rights.
To be able to reduce such a catalogue of rights to those that are actually relevant for the evaluation, a preliminary evaluation is necessary.
3.4.1.1 Type and Functions of the Security Measure
At the beginning of the evaluation, a certain security measure will have been selected for evaluation, based most likely on criteria like effectiveness in providing security and overall costs. This means that the very start of the procedure is the decision in favour of a certain measure, for instance a system for biometric access control or video surveillance.
To make this decision in a professional way, at the very least some basic technological knowledge, as well as knowledge in the fields of security and counter-terrorism are required. Here scenarios and scenario building tools can be helpful, as they give indications for the necessity and suitability of a measure. The second pillar of decision making in this context are the technological and social features of a security measure. Ideally, the decision maker should rely on more than his or her own expertise, but consult other experts and gather second opinions in order to ensure that the facts gathered in this phase of the evaluation are sufficiently robust.
At the end of this step, type and functions of the security measure that is to be evaluated will be identified.
3.4.1.2 Fundamental Legal Provisions
After the basic functions of a measure have been isolated and carved out, the fundamental legal provisions can be identified. To do this, it is necessary for the user to possess legal knowledge. A fundamental right or principle is relevant, if its protected sphere is affected by the measure being evaluated. Furthermore, a fundamental right can become relevant where it is facilitated by the measure. To determine this, the chances and risks of the use of the security measure relative to the exercise of fundamental rights and principles have to be examined. These chances and risks are derived from the functions identified in the previous step. This is in line with the target to extract legal requirements from social principles that are the basis for legal norms. Depending on type and functions of a security measure, different fundamental rights will be affected.
It has to be noted that the goals stated in fundamental rights do not just stand side by side, but that they often come in conflict with each other, meaning there are conflicts of goals.57 Such conflicts can occur in every stage of the method. They should not be solved immediately if possible, but instead be carried on as far as possible in order not to lose alternative solutions that may result from these conflicts of goals. This enables the user of the proposed method to balance different fundamental rights issues in the final stage of the use of the method (e.g. issues relating to human dignity, bodily integrity, privacy and so forth) and even to put an emphasis on the resolution of one issue in favour of another when ultimately choosing a security measure. The method is not meant to impose on the user which fundamental right is more important in case of a conflict, and indeed it cannot do so since the answer depends on the individual case at hand. Instead, the additional value of the use of the method in regard to conflicts is that its use will reveal the existence of such conflicts and uncover alternative solutions for individual fundamental rights issues. By revealing conflicts, the method helps to prevent and correct any one-dimensional maximisation of an individual target value.58
The carved out functions and the fundamental legal provisions should be linked in a table in order to increase clarity and traceability of the process (Fig. 3.3).
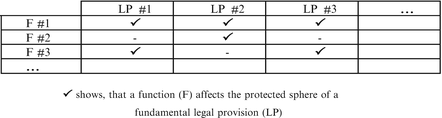

Fig. 3.3
Example of a diagram of the functions of a security measure and the affected fundamental rights
3.4.2 Stage 1 – Deduction of Legal Requirements
What follows is the first step of the concretisation process in which the fundamental legal provisions are condensed and channelled into legal requirements. Where such concretisations already exist, for example in the shape of a court ruling, they can be resorted to. In any other case, the conventional methods of legal interpretation should be used.59
The legal requirements are the product of the legal interpretation of social functions that are affected by the technology being evaluated. This makes it necessary to establish a relation between the fundamental legal provisions and the social functions of the technology.60 The goal of this first step of the use of the method is to create legal norms that have been specified for the technological environment. The legal requirements are expressed in legal terminology.
Two important aspects have to be kept in mind from the very start of the use of the proposed method:
The principle of proportionality61 can neither serve as a fundamental legal provision nor as a requirement; rather it is an implicit part of the method. This results from the fact that the question of the proportionality of a measure – and thus of the material lawfulness – is an aspect of legal compatibility, which aims at a gradation of proportionality. Proportionality is thus not located on the level of legal requirements, but instead it is an overarching concept that lances the evaluation as a whole and which is ultimately absorbed by the concept of legal compatibility.
The method does not restrict the evaluation to technological aspects of a security measure. Instead, organisational aspects have to be considered as well during the use of the method. This results from the fact that a security measure that has been acquired as a result of a positive evaluation then has to be implemented. This implementation – the organisational design of the newly acquired security measure – is equally important for the realisation of fundamental rights as the technological design of the measure, since a measure could be designed in a way to respect fundamental rights very well, but then be implemented in a way that negates this, e.g. through abusive security staff. It is of paramount importance to derive organisational solutions to fundamental rights issues together with the technological solutions since a security measure may be designed in a way that makes it impossible to realise a certain organisational requirement or that would make significant alterations necessary. Therefore, a decision maker has to be aware of these organisational solutions before a decision is made in favour of a certain security measure.
3.4.3 Stage 2 – Concretisation into Legal Criteria
The legal requirements are now concretised into legal criteria by deriving from the legal requirements the basic requisites concerning the use of the security measure. In order to do this, rules have to be identified which determine how to fulfil the legal requirements with regard to the specific features, risks and conditions of the use of the security measure.62 The criteria thus derived are both connected to the technology as well as to the social and legal aspects. They are the bridge between the law and technology and herald a change in terminology from the legal terminology to the terminology of technology. This means that while the language used becomes more and more technical during the process of concretisation, the legal criteria form the threshold between legal terminology and technical terminology.
Legal criteria describe solutions for the problems within the legal requirements, but without a limitation to a certain concrete technological, organisational or legal approach. All technical and non-technical possibilities for solutions still remain possible at this stage.63
3.4.4 Stage 3 – Concretisation into Technical Objectives
On the third stage, technical objectives are derived from the legal criteria by looking for the most basic functions that the technology has to have in order to fulfil the demands set by the legal criteria. Since they can also contain organisational objectives that do not pertain to the concrete design of a technology, but rather to the environment and manner of its use, they could also more accurately be called technical and organisational objectives. The technical objectives are abstractions of concrete technological features. The concretisation of legal criteria is based on considerations about how to transform these legal criteria into basic functions of a security measure including organisational aspects. The objectives thus developed are descriptions of functions and technical requirements in general terms.
On this stage, alternative proposals can be developed to have a broader basis for the comparison following in the final stage. Such alternative proposals can also facilitate a comparison between several security measures that try to give different solutions to legal requirements.
The objectives derived should indicate how to best adhere to fundamental legal provisions. This means that they will often go beyond minimum legal requirements and it also means that conflicts between objectives will arise. The security measure that is ultimately chosen by the decision maker should be the one that best fulfils the technical objectives and that best strikes a proper balance between conflicting objectives.
3.4.5 Stage 4 – Comparison
The use of the method concludes with a comparison of security products with the technical objectives developed in the previous stage. If the user evaluates more than one security measure, he or she is advised to draft a table containing an overview as shown in Fig. 3.4. Alternatively, the technical objectives can be used as a checklist for the selection of a suitable security measure. It has to be kept in mind that it is possible for a security measure to only partially comply with a technical objective. Also, when comparing several security measures, the situation can occur that a number of candidates are equally compatible with technical objectives. In such a case the user should fall back to non-legal factors to decide between these candidates.
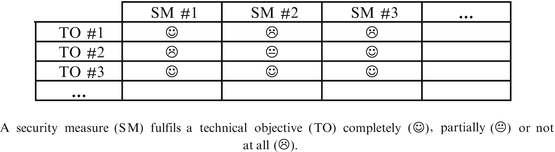

Fig. 3.4
Example of a diagram when comparing security measures
After a security product has been purchased, the organisational objectives which have been developed in stage 3 as a side-product come into play, as well as technical objectives which take a dual function by containing both purely technological and purely organisational aspects. They give advice to the decision maker how to implement the new security measure and which organisational structure surrounding the measure he or she should choose.
For a summary illustration of the structure of the method see Fig. 3.5.


Fig. 3.5
A method for the legal evaluation of security measures; SMT Security Measure or Technology
3.4.6 Alternative: Stage 4 – Technical Design Proposals
As an alternative to stage 4 as described above, the technical objectives that have been developed over the course of the use of the method can be further refined into technical design proposals.64 Thus, the method can be of interest not just to end users of security measures, but also to manufacturers and developers in the security sector that want to benefit from the continuous boom in demand, by enabling them to develop security products that are legally compatible and that hence can survive in the marketplace and prevail in the critical eyes of the public. Furthermore, end-users can use the design proposals to demand improvements and reworking of a product from its manufacturer; thus exerting influence on the technological design of a security measure.
Technical design proposals are a collection of measures for direct implementation into the technology.65 They are often not without alternatives; they should be seen as proposals, as their name indicates. This means that, just as the technical objectives, the catalogue of measures created in this last step can contain several alternative solutions for an individual problem. This is due to the fact that the aim is not to create a coherent system design. In fact this cannot be the case as the method only looks at those aspects of a technology that are legally relevant. However, the proposals developed should be fit for direct implementation. This means that they have to be concrete enough that they could become part of a technical specifications sheet.66 Their implementation may not be strictly necessary from a legal point of view, but it should at least be desirable. This is due to the fact that the results of the use of the method have been designed to fulfil fundamental legal provisions in the best way possible which means that they can be above the legally required minimum standard.67
During the creation of a technology, the technicians, engineers, etc. involved can work towards the implementation of these measures. The method would then come into play during the design phase of technology development, after a technology has been defined beyond the early stages of conceptual development.68 This means that there already has to be some idea about composition and capabilities of a technology, i.e. ideally after an early prototype has been constructed.
If the method is used in this context, those technical objectives which are not strictly concerned with technology design, but rather with the use of technology and its organisation, must not be omitted; they remain relevant. Already in the early stages of the design process it has to be made sure that technology is designed in a way that does not hinder or preclude certain legally compatible organisational options.
A good example of this would be a hypothetical technical objective that demands that the person evaluating images created by a body scanner is located out of sight of the scanner. If the manufacturer does not implement the capability to transmit the images to another location (and if this feature cannot be added later), then security personnel evaluating the images can only be situated directly at the device; thus making it impossible to implement the objective.
Quite the contrary, producers should work towards promoting certain organisational options which benefit fundamental rights. To that end, it is imperative that producers concern themselves with organisational aspects and possibilities of the later use on the level of technical objectives and design proposals, and account for them in the development process. Fundamental rights would benefit even more, if producers were to pass recommendations for the implementation of their products and its organisational environment on to the buyers and users. In order to realise this, it is again necessary for producers to concern themselves actively with these aspects.
If used during the development of a security measure, the aim and effect of the method is avoiding or at least minimising the immanent risks of a technology before introducing a product to the market. Risk in this context means any negative effect or impact that a technology might have. Another aim is the achievement or strengthening of chances, meaning positive consequences.69
3.4.7 Example of Use
As was shown above, body scanners are a highly controversial technology. This means that they are well suited to provide a short and simplified example of the use of the methodology proposed in this chapter.
The basic functionality of a body scanner can be summarised as follows. A body scanner:
irradiates the body with electromagnetic radiation,
penetrates clothing,
creates an image of the naked human body, and
detects objects hidden on the body and in clothing.
Fundamental rights and principles of the Charter of Fundamental Rights of the European Union affected by the use of full body scanners – derived from the chances and risks behind the technology – are:
Article 1 CFR – Human dignity,
Article 3(1) CFR – Right to the integrity of the person,
Article 4 CFR – Prohibition of torture and inhuman or degrading treatment,
Article 7 CFR – Respect for private and family life,
Article 8(1,2) CFR – Protection of personal data,
Article 10(1) CFR – Freedom of thought, conscience and religion,
Article 21(1) CFR – Non-discrimination,
Article 24(2) CFR – The rights of the child,
Article 25 CFR – The rights of the elderly,
Article 26 CFR – Integration of persons with disabilities,
Article 35 CFR – Health care, and
The rule of law.70
A complete evaluation would go beyond the scope of this contribution. The following is an excerpt of how such an evaluation would look like.71 The information above forms the basis of the evaluation and is a summary of the results of what would happen in the pre-stage of the evaluation.
The underlying scenario shall be the planned introduction of full body scanners at a European airport. For the first example, Article 35 CFR has been selected to demonstrate the different steps of concretisation from fundamental legal provisions to legal requirements, to legal criteria and ultimately to technical objectives. The second example will show how conflicts emerge and how to deal with them. Finally, the third example will give an instance of the derivation of an objective that is concerned with organisational aspects.